MediaTek: A Short Story
Finding that you have a MediaTek device which has its Boot ROM interface disabled land on your desk?
Access to MediaTek’s Boot ROM interface is the best way to extract the maximum amount of data from any device with a MediaTek chipset. The Boot ROM is always there, and it will not change. Because of this, we do not have to worry about different vendors, firmware, or security patches. It just works.
Earlier this year we released a blog post titled “How to Use XRY to Extract Data from MTK-Based Devices” which showed our solution to recover all data, BFU.
Since then, some vendors have decided that access to the Boot ROM is not necessary and released a patch that caused our solution to stop working. Which, of course, was frustrating for us and prevents you, our customers, from creating a successful extraction from MTK based devices.
However, there is still a way to access it…
Some disassembly required
Luckily for us, MediaTek’s Boot ROM is written in a way that during the boot process it will read the storage (eMMC or UFS) and depending on the content, it will decide what to do next, usually the Android operating system is then loaded. But the keyword here is “read”. If there is no storage to read, there is no Android to boot and instead the much-appreciated interface we want boots that then allows access.
We could remove the storage chip but that would prevent us from being able to read the data ourselves. If we instead, short the storage CLK or DATA to ground during the boot process it cannot be read, and the door opens. After connection is established, we release the short immediately and our loader can access everything like normal.
There is just one small caveat. Just like Intel, the storage chips are on the inside and some disassembly is required to get physical access. We consider this as a last resort and because of that we would recommend using our Access Services who can assist with the disassembly and extraction. Access Services are delivered in one of our secure MSAB forensic facilities using forensically sound techniques with written documentation of every step.
For the brave
With access to the right equipment, or if you feel MacGyver is more your style, it is not too hard to disassemble a device and locate the storage chip.
Devices today usually use adhesive; for disassembly, you may need a heating element to loosen and remove the case for it to be successful. When the device is open, it is time to locate the storage chip, usually on the rear of the motherboard, behind RF shields. With a little bit of luck, you will find just snap-on shields or metallic tape covering the components. If unlucky, you will have to desolder the shields or try to prize them off, potentially risking damage to the motherboard.
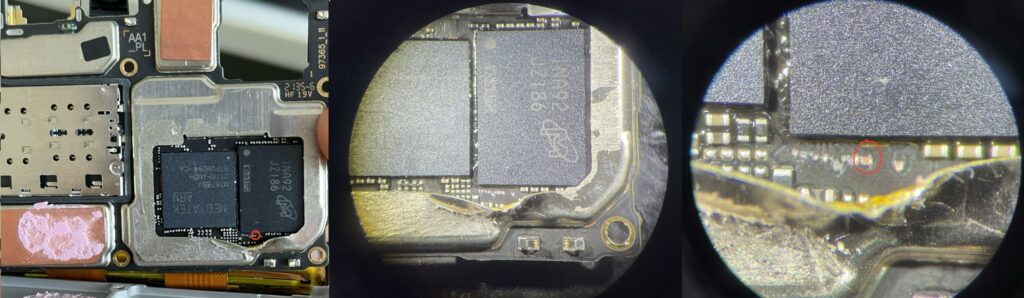
With the shields removed you should see the MediaTek SoC and eMMC/UFS chip. Located between and/or around the chips there are usually some test points for storage CLK and DATA. They might be covered with paint and/or epoxy which would then require delicate scraping to remove before we can short them to ground during the boot process.
The following example is from an Oppo A16s CPH2271 where the test points were covered with paint.
In our Customer Portal you will have access to a document named “MSAB – MTK Boot ROM Exploit Test Point Guide”. It includes pictures of known test points for many different devices and hints on how to open them.
End of life
For forensics sake, be careful taking things apart, or contact Access Services for complete peace of mind. We will gladly help with complex extractions and/or help locate the correct test points for your case.
MSAB, we do what we must, because we can.
 About the author:
About the author:
Christoffer Maliniemi is a Security Researcher at MSAB with over two decades of software engineering experience. Driven by curiosity, he has been contributing to our team since 2020.

 About the author:
About the author:

